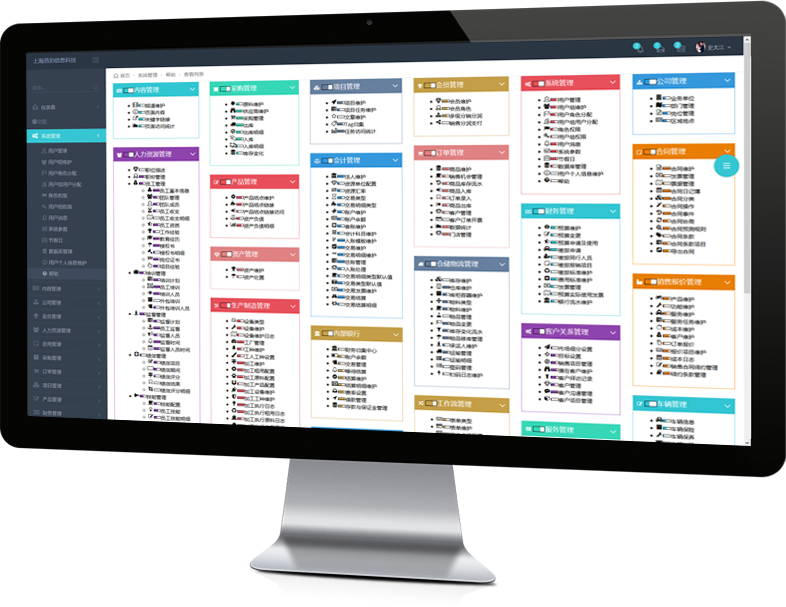
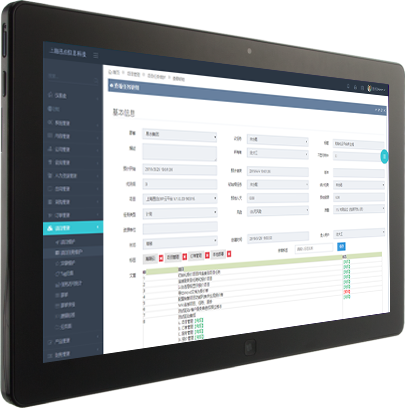
The stocking and outbound relationship of goods query inventory by time
Business information in transactions is required to be kept confidential. If the credit card's account number and username are known, they can be stolen, and if the order and payment information is made available to competitors, the opportunity may be lost. Therefore, there is an encryption requirement in the transmission of information in e-commerce. As businesses grow from small to large, ther
Know moreThe stocking and outbound relationship of goods query inventory by time
Functional website is also known as custom website, it is different from the general kind of only article pictures and video-like sites, more biased in the application of logic processing, customization is strong. Some enterprises have special requirements for the functionality of the site, which makes functional development for these requirements, so the price of such sites is higher. The cost
The stocking and outbound relationship of goods query inventory by time
Public key encryption, also known as asymmetric encryption. The typical asymmetric encryption algorithm RSA algorithm was developed by the study of Rivest, ShamirandAdlerman. It is based on the combination of large prime number factors and the difficulty of factor decomposition, that is, its confidential ity is based on computational complexity. A 150-bit or so combined number, even with the cur
Comprehensive consulting
One-stop consulting on corporate businessprocesses, data models, servers, websites, integrations, apps,cloud platform construction, new media operations, etc.
Professional Services
Pre-sales, integration, implementation, cooperation begins with communication
After sales service
After-sales, maintenance, reliable and stable partners
Technical support
Customer community, technical materials, version updates, best practices, strong backing
stocking